���� >�N��
Mirai�c�N�{�����Q�P���d
��������ۻO�W�j�ǭp�ꤤ�ߥ_�ϾdzN��T�w�����B����
�ͬ��b����k�o�F���ɥN�A�X�G�C�ӤH���ܤ־֦��@�䴼�z������A�\�h���Ҥ]���ѧK�O���L�u�����ѤH�ϥΡC�j�a�O�_��ҹL�A�b�z���䪺���p��(IoT)�˸m�A�γ\�w�g�D�����H�h�����ӤJ�c�N�{���F�O�H
�ھڥh�~iThome���@�g���ɡG�u�b�ȭ̦b�����¤W�o�������A�Q�n�X���HMirai�c�N�n�鬰�D���L�ͺ����A���L�ͺ����ұ���˸m�ƶq�w�F��|�Q�U�ӡv�C�q�o�g���ɬݨӡA��Mirai�P�V���˸m�ƶq�e�j�A�p�G�Q�Τj�q��IoT�˸m�����Y�@�ؼСA�ҳy�����l���N���H���p�C
�ثeMirai�D�n�������覡�O�Τ��������_�A�ȧ���(Distributed Denial of Service �w DDoS)�A�ت��O�n���ȧ����ؼЪ������A�ȡC�h�~�o�L�Ʀ��z�LMirai�ޱ���DDoS�����A�Ҧp�h�~�Q��ADyn���q���Ѫ�DNS�A�ȳQDDoS�����A�ɭP�@�Ǻ����L�k���`�B�@�C
�b�ϥΰ�����~���P�ɡA��b���M�I�]�@���s�b�ۡC�j�a�i�H�z�L�\Ū���g�峹�A�i�@�B�F��Mirai�C
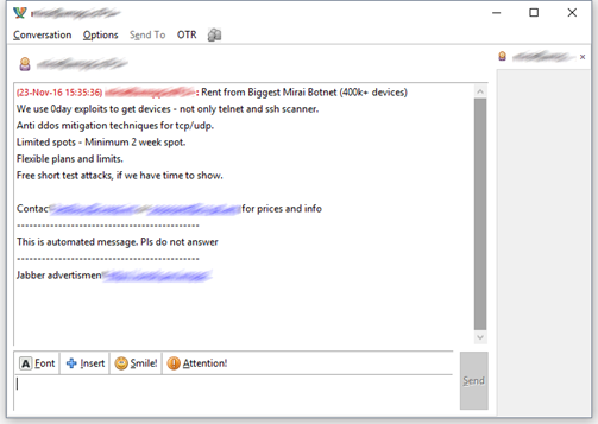
�Ϥ@�G�X��Mirai���s�i�T��
Mirai����
Mirai�O�@�Ӵc�N�n��A�����欰���{�����q��į�ΡCMirai���D�n�P�V�ؼЬO���p���˸m�F���˸m�Q�ӤJMirai��A�����̥i�H�ޱ��Ӹ˸m�A�B��Ӹ˸m���ܬ��L�ͺ����������A�����̥i�Q���L�ͺ����i��j�W�Һ��������CMirai����l�X(Source Code)�w�g�b�b�Ƚ¤��}�A�H�}����l�X(Open Source Code)���Φ��o���A�N�ɭP�J�IIoT�]�ƪ��N�A�i��Φb��h�s���c�N�n��W�C
���p��(Internet of Things�A²��IoT)�A�s�x�w�q���U���˸m�]�Ƴz�L�s�W���ں����A���۫إ߳s�u�H�ǰe�P������T(�άO���)�C�Ҧp�����L�����B���z���q���B�����ʱ���v���B�a�θ��Ѿ��H�ιq���Ϋ~�����A���O���p�����˸m�C
��Mirai�����欰
(�@) ��Mirai�P�V���˸m�A�|����a�b���ں����W(���q�ۦP���q�}�l�A�����X�i��~��)���y���p���˸m��IP��}�M�s����C
(�G) ���y���L�����P�V�˸m��IP��}�M�s���𤧫�AMirai�|�q�L�h�ر`�ιw�]�b���M�K�X���է����Ӹ˸m�A�p�G�i�H�n�J�Ӹ˸m�A�H�Y�}�l�w��Mirai�C���M���P�V���˸m�W�ݰ_�ӥ��`�B�@�A�����ɭԷ|���ǩ���A�ӥB�����W�e�y�q�]�o�Ͳ��`���p�C
(�T) Mirai���\�P�V��A�|�R���Ӹ˸m�W�P�������c�N�n��A�ӥB�|�������ݺz�s����C
(�|) �u�n�˸m�����s�ҰʡA�|�@���B�b���P�V�����A�C�@���˸m���s�}������Mirai���|�B�@�A���O�u�ɶ����Ӹ˸m�٬O�ܦ��i��Q�P�V�C
Mirai������k�G���������_�A�ȧ���
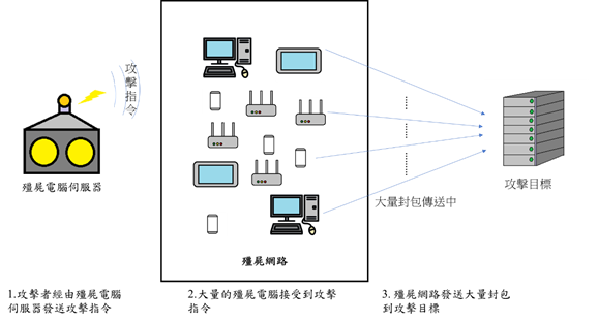
�ϤG�GMirai DDoS�����ܷN��
DDoS�����O���_�A�ȧ���(Denial of Service �w DoS)���i�����CDoS�O�@�شc�N��������k�A�����̷|�ϥΦh�ؤ覡��ؼжǰe�j�q���ʥ]�A�ín�D�ؼжǰe�^�аT���A���ؼЪ������W�e�ֶ�άO�t�θ귽�ӺɡA�y���ؼеL�k���ѪA�ȵ��ݭn���ϥΪ̡C
�HDoS��������¦�ADDoS�����O�Q�Ψ�ƶq�e�j���L�q���ҫإߪ��L�ͺ����ӵo�ʤj�W�ҧ����A���ا����i�H���ؼЪ��A�ȼȮɵL�k���ѡC���ߤH�h�Q�γo�ؤ覡�i��c�N���ӷ~���ʩάF�v�欰�A�Ҧp�����ӷ~�W���v�����B���ȧ벼�������C
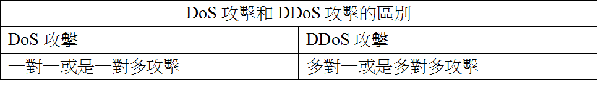
��ij���I
1. �ʶR���p���˸m�ɡA�ݽT�{�˸m��ק�b���K�X�F�ϥΫe�A�ק��˸m���w�]�b���K�X�A�إ߱j�����K�X(�^��j�p�g�B�Ʀr�Ÿ��V��)�C
2. ���p���˸m���n�骩���ݩw����s�A�H����ߤH�h�Q�κ|�}���o�˸m�ϥ��v���C
3. ���������p���˸m���ϥΪ��A��(�Ҧp���ݦs���\��)�C
�ѦҸ��
1. ������C2016-11-30�C40�U�˸m��Mirai�L�ͤj�x���M�W�����}�X���CiThome�C���}�Ghttp://www.ithome.com.tw/news/109941�C
2. Mirai(�c�N�n��)���СC����ʬ�C���}�Ghttps://zh.wikipedia.org/wiki/Mirai_(%E6%81%B6%E6%84%8F%E8%BD%AF%E4%BB%B6)�C
3. Symantec Security Response�C2016-10-27�CMirai: what you need to know about the botnet behind recent major DDoS attacks�C���}�Ghttps://www.symantec.com/connect/blogs/mirai-what-you-need-know-about-botnet-behind-recent-major-ddos-attacks�C
4. �������C2016-02-18�CWordPress Pingback DDoS�������R�C���}�Ghttp://cert.ntu.edu.tw/Document/TechDoc/Analysis_of_WordPress_Pingback_DDoS_Attack.pdf�C
5. TREND LABS�Ͷլ�ޥ��y�N�䴩�P��o���ߡC2014-09-15�C�mIoT���p���w���Ͷաn���ʴ��z���˸m�Ӫ`�N�Ǥ���H���}�Ghttps://blog.trendmicro.com.tw/?p=9617
6. ���p���w�q�C����ʬ�C���}�Ghttps://zh.wikipedia.org/wiki/%E7%89%A9%E8%81%94%E7%BD%91
�Ϥ��ӷ�
1. Mirai�X�ɪ��s�i�A�ӷ����}�Ghttps://www.bleepingcomputer.com/news/security/you-can-now-rent-a-mirai-botnet-of-400-000-bots/�C
�P��
�P�¥_��ASOC���B�ζ����ѧN��T