- Date:2017-5-24
May 12, 2017, a new transformed ransomware WannaCry(WannaCrypt0r 2.0) exploded, no need to open a single file or a website, a mere internet connection could cause attack, infection, and data blocked for ransom. The ransomware evolved into a new variation combining a SMB protocol vulnerability in Windows, which appears to have used a flaw in Windows XP/Vista/7/8/8.1 to spread rapidly across network in 150 countries.
Cyber-attack
Once the hacker found a vulnerable computer with a SMB vulnerability exposing port 445 on the Internet, they inject ansomware into the computer and continue to scan other computer, repeating the attack and poisoning.
Self-detect setps
- Turn of the Internet connection(both wired and wireless network)
- Check System Explorer, if you see taskche.exe or mssecsvc.exe, shut down the computer(cut of the power source), you are already infected.
- Reboot in the safe mode(F8), copy the remaining unblocked files. Or just simply reformat your computer.
- Basically, Windows 10 would not be infected, though when the browser came up with a warning message, DO NOT click download restoration, it’s another way to activate the virus.
Self-detect setps
- Open Windows Update and update to restore the system flaw.
- Backup data files( no need for system files)
- Be careful when opening website links and files
- Install anti-virus software and keep the update for virus code on
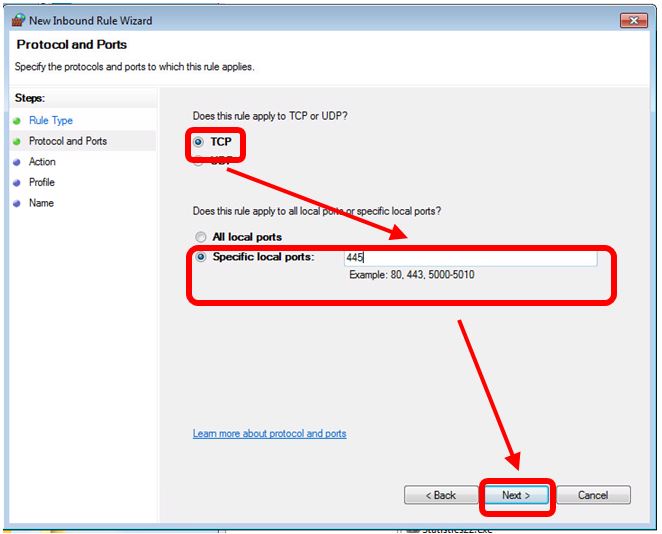
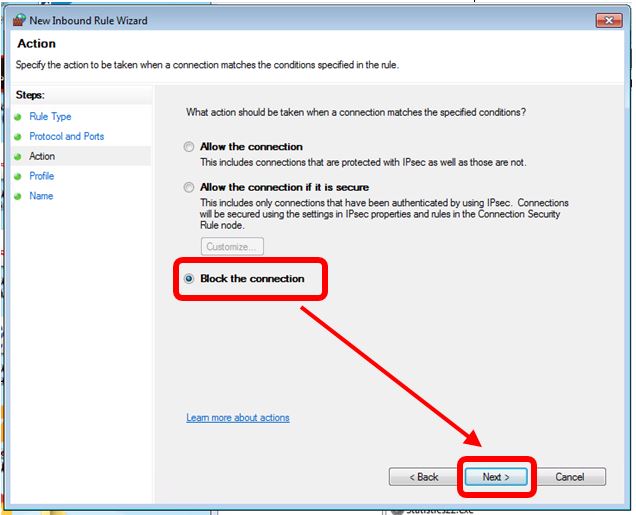
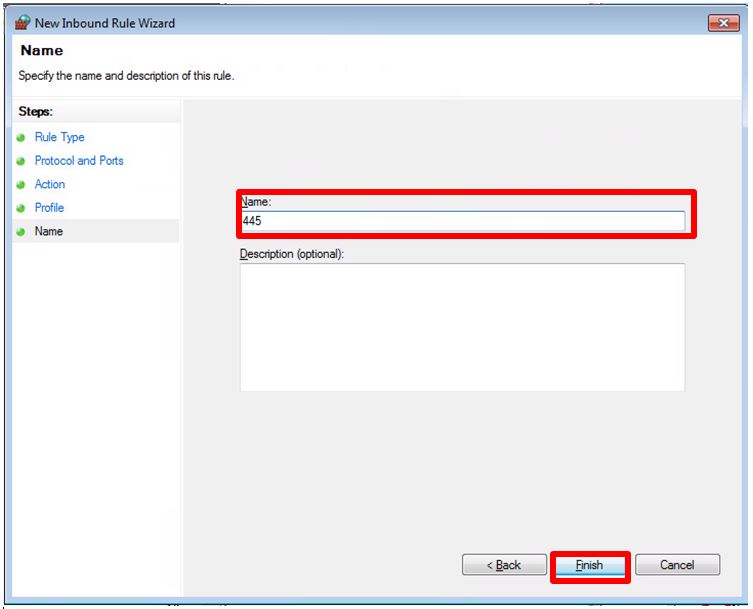
- Block the TCP port 445(shown on the following pictures)
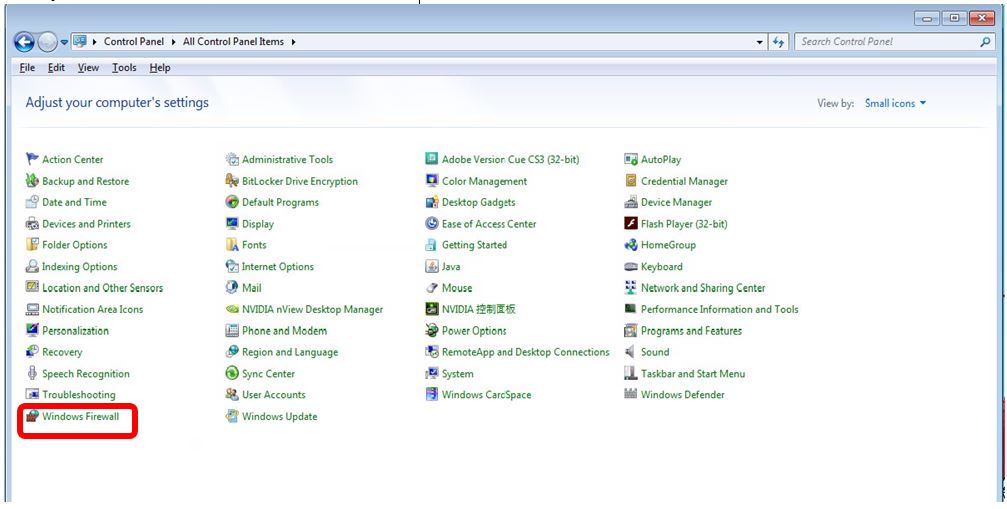
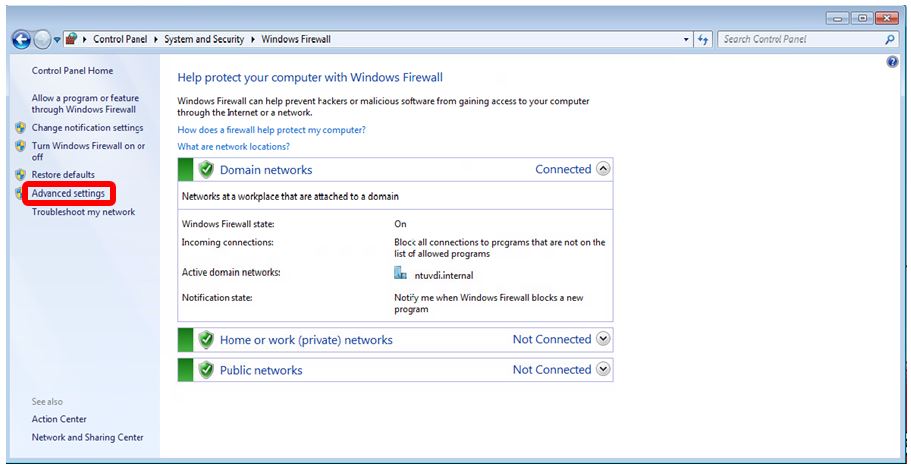
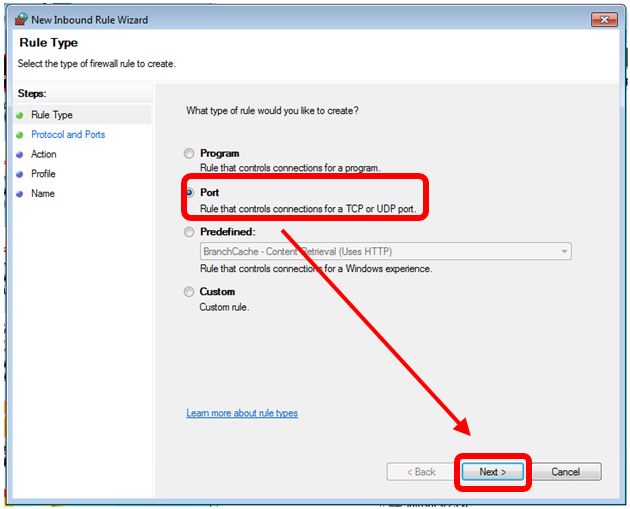
Steps for blocking TCP port 445:
Step1: Start ->control -> click control Panel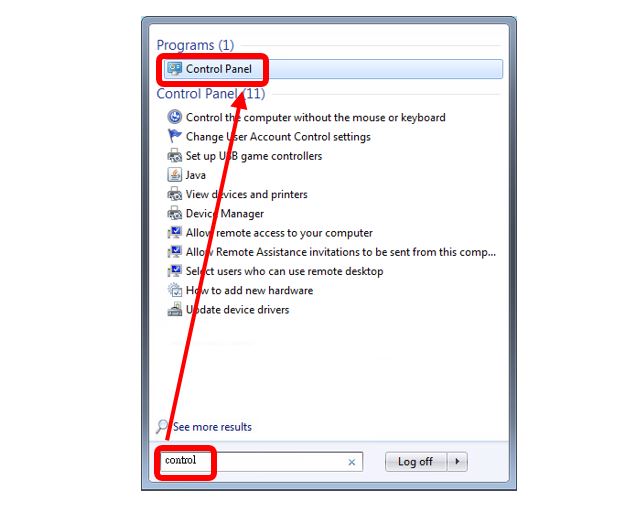
Step 4 : click Inbound Rules the left coloumn, then New Rule on the right column.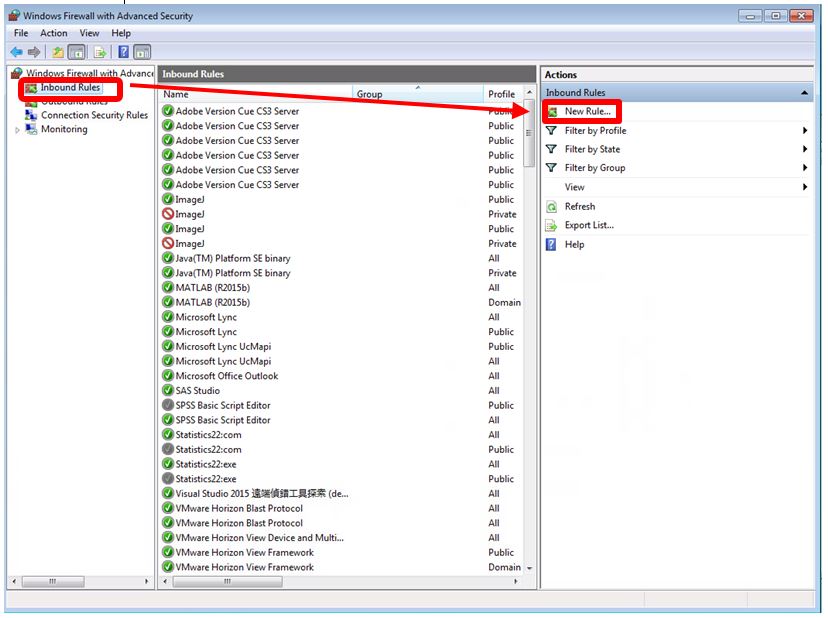
Step 6 : select TCP - > Specific local ports -> add 445 -> next